
Detecting HashiCorp Vault Policy Changes
Security of a HashiCorp Vault deployment is of paramount importance given the sensitive nature of the information contained within the platform. …

Security of a HashiCorp Vault deployment is of paramount importance given the sensitive nature of the information contained within the platform. …

How do we verify that the Terraform binary we download is the same as the one HashiCorp produced? Ensuring the integrity of software is important to …

Signing software has become critically important given the recent supply chain attacks. How do we verify that the software we’re downloading is …

One of the major benefits of using the public cloud is the integrated identity and access management (IAM). This simplifies the process of granting …
HashiCorp Vault supports several authentication methods for human and non-human access. Several of the non-human authentication methods are tied to …

HashiCorp Vault supports a number of authentication methods including methods that utilize what HashiCorp refers to as a “trusted …
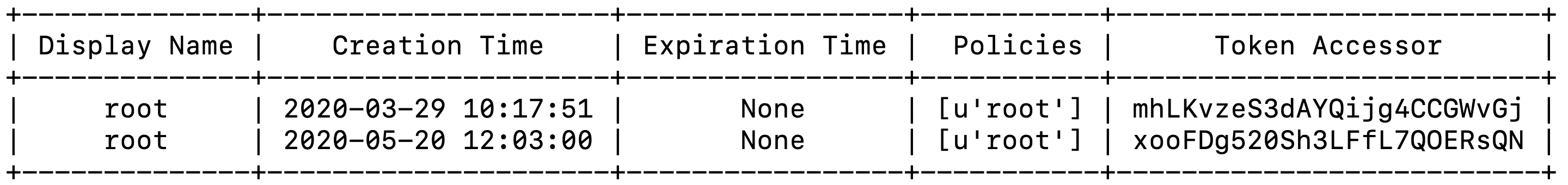
Revoking the root token on a production HashiCorp Vault deployment is one of the recommended best practices for securing an instance of HashiCorp …

HashiCorp Vault generates a default root token during installation and best practice dictates that the token should be revoked once the deployment has …

Security of a HashiCorp Vault deployment is of paramount importance given the sensitive nature of the information contained within the platform. …
HashiCorp Vault is quickly becoming the defacto secrets management platform used in environments that rely on DevOps concepts for application …

Vault (https://www.vaultproject.io/) is a secrets management tool created by HashiCorp that is extremely popular. Given the sensitive nature of the …

In this post we’ll walk through how we can utilize vRealize Orchestrator and Splunk to determine how compliant our vRA appliance is with the …