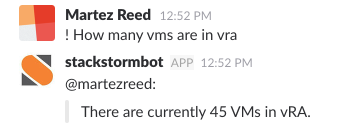
vRA7 Chatops with StackStorm
ChatOps is a pretty cool and still emerging technology that allows users to initiate actions on external systems from within a messaging platform such …

In this post we’ll walk through how we can utilize vRealize Orchestrator and Splunk to determine how compliant our vRA appliance is with the vRealize Automation 7.2 hardening guide.
The first task is utilizing a script to check the settings specified in the hardening guide. In our case we’re going to generate JSON output from the script in order to easily ingest the data into Splunk. We’re utilizing bash to avoid any dependencies upon other packages that aren’t part of the default appliance install. The script below has been truncated for brevity and can be found in the github repo (https://github.com/martezr/vra72-hardening-automation).
The script is incomplete and does not cover all the items covered in the hardening guide.
#!/bin/bash
# Set host variable as the system hostname
host=$(hostname)
header="{ "host": "$host", "checks": ["
checks=""
checknumber="011"
checkdescription="Use IPv4 TCP Syncookies"
cat /proc/sys/net/ipv4/tcp_syncookies | grep -v 1 > /dev/null 2>&1
if [ $? -eq 1 ]; then
check="{"check": "$checknumber","check_description": "$checkdescription","status": "pass"},"
checks="$checks $check"
echo "pass"
else
check="{"check": "$checknumber","check_description": "$checkdescription","status": "fail"},"
checks="$checks $check"
echo "fail"
fi
checknumber="012"
checkdescription="Deny IPv6 Router Advertisements"
grep [01] /proc/sys/net/ipv6/conf/*/accept_ra|egrep "default|all" | grep -v 0 > /dev/null 2>&1
if [ $? -eq 1 ]; then
check="{"check": "$checknumber","check_description": "$checkdescription","status": "pass"},"
checks="$checks $check"
echo "pass"
else
check="{"check": "$checknumber","check_description": "$checkdescription","status": "fail"},"
checks="$checks $check"
echo "fail"
fi
echo "{ "host": "$host", "checks": [${checks::-1}] }"
The script will generate JSON output similar to that below.
{
"host": "vratest.grt.local",
"checks": [{
"check": "011",
"check_description": "Use IPv4 TCP Syncookies",
"status": "pass"
}, {
"check": "012",
"check_description": "Deny IPv6 Router Advertisements",
"status": "fail"
}, {
"check": "013",
"check_description": "Deny IPv6 Router Solicitations",
"status": "pass"
}, {
"check": "014",
"check_description": "Deny IPv6 Router Preference in Router Solicitations",
"status": "fail"
}, {
"check": "015",
"check_description": "Deny IPv6 Router Prefix",
"status": "fail"
}, {
"check": "016",
"check_description": "Deny IPv6 Router Advertisement Hop Limit Settings",
"status": "fail"
}, {
"check": "017",
"check_description": "Deny IPv6 Router Advertisement Autoconf Settings",
"status": "fail"
}, {
"check": "018",
"check_description": "Deny IPv6 Neighbor Solicitations",
"status": "pass"
}, {
"check": "019",
"check_description": "Restrict IPv6 Max Addresses",
"status": "pass"
}]
}

The first task in the workflow is to dynamically generate the command to run on the vRA appliance. In this example the script is stored on a web server and one of the workflow inputs is the url of the script.
script = 'curl -so script.sh ' + scriptUrl + ' && chmod +x script.sh && sh script.sh; rm script.sh';
The second task is running the generated command against the vRA appliance and capturing the JSON output into an attribute that will later be sent to the Splunk server.
The third task in the workflow is to fetch the FQDN of the VM to be used as the source for Splunk.
splunkSource = vm.guest.hostName
The final task in the workflow is to send the JSON output from our compliance script to our Splunk server. For this task we’re going to utilize the Splunk REST API to send data to the Splunk server. Before we can post the data we need to setup our REST API endpoint in vRO.
Library > HTTP-REST > Configuration > Add a REST host

Select “Basic” host authentication

We’ll select “Shared Session” for the session mode and enter in a Splunk user account with the appropriate permissions. Click “Submit” to add the REST host.

Now that we’ve added our REST host we just need to add a REST operation.
Library > HTTP-REST > Configuration > Add a REST operation
Select the REST host that we just created as the “Parent Host”. Copy and past the “Template URL” below which utilizes a variable for the source name that was defined in the previous workflow step.
/services/receivers/simple?source={sourceName}&sourcetype=web_event

Now that we’ve got our compliance data being ingested into our Splunk server let’s turn that data into a dashboard to easily make sense of the the data.

http://theithollow.com/2015/08/27/vrealize-orchestrator-rest-hosts-and-operations-for-rubrik/

ChatOps is a pretty cool and still emerging technology that allows users to initiate actions on external systems from within a messaging platform such …

A recent blog post by Rob Nelson about using vRO to provision VMs with vSphere tags …